Check whether it shows lot of SYN_WAIT / TIME_WAIT / FIN_WAIT. If yes its due to the high number of connections. You can reduce these by adding some rules to the Iptables.
# iptables -A INPUT -p tcp --tcp-flags SYN,FIN SYN,FIN -j DROP
# iptables -A INPUT -p tcp --tcp-flags SYN,RST SYN,RST -j DROP
# iptables -A INPUT -p tcp --tcp-flags FIN,RST FIN,RST -j DROP
# iptables -A INPUT -p tcp --tcp-flags ACK,FIN FIN -j DROP
# service iptables save
# service iptables restart
Adding rules to sysctl.conf
Also you can reduce these by adding some rules to sysctl.conf, the details given below.
# echo 1 > /proc/sys/net/ipv4/tcp_syncookies
Put following in /etc/sysctl.conf
# Enable TCP SYN cookie protection
net.ipv4.tcp_syncookies = 1
# Decrease the time default value for tcp_fin_timeout connection
net.ipv4.tcp_fin_timeout = 30
# Turn off the tcp_window_scaling
net.ipv4.tcp_window_scaling = 0
# Turn off the tcp_sack
net.ipv4.tcp_sack = 0
Then execute the command :
A quick and usefull command for checking if a server is under ddos is:
# netstat -anp |grep 'tcp\|udp' | awk '{print $5}' | cut -d: -f1 | sort | uniq -c | sort -n
Reference : http://linuxhow2.net/?p=9
# Set default policies
/sbin/iptables -P INPUT ACCEPT
/sbin/iptables -P OUTPUT ACCEPT
/sbin/iptables -P FORWARD DROP
/sbin/iptables -F
/sbin/iptables -F INPUT
/sbin/iptables -F OUTPUT
/sbin/iptables -F FORWARD
/sbin/iptables -F -t mangle
/sbin/iptables -X
/sbin/iptables -A INPUT -i lo -j ACCEPT
/sbin/iptables -A INPUT -d 127.0.0.0/8 -j REJECT
/sbin/iptables -A INPUT -i eth0 -j ACCEPT
/sbin/iptables -A INPUT -m state --state INVALID -j DROP
### chains to DROP too many SYN-s ######
/sbin/iptables -N syn-flood
/sbin/iptables -A syn-flood -m limit --limit 100/second --limit-burst 150 -j RETURN
/sbin/iptables -A syn-flood -j LOG --log-prefix "SYN flood: "
/sbin/iptables -A syn-flood -j DROP
Reference : http://www.webhostingtalk.com/archive/index.php/t-355411.html


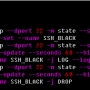 iptables를 이용한 SSH brute force 공격방어
iptables를 이용한 SSH brute force 공격방어